High-bandwidth Digital Content Protection (HDCP) is a form of digital copy protection developed by Intel Corporation to prevent copying of digital audio and video content as it travels across connections. Types of connections include DisplayPort (DP), Digital Visual Interface (DVI), and High-Definition Multimedia Interface (HDMI), as well as less popular or now deprecated protocols like Gigabit Video Interface (GVIF) and Unified Display Interface (UDI).
VOB is the container format in DVD-Video media. VOB can contain digital video, digital audio, subtitles, DVD menus and navigation contents multiplexed together into a stream form. Files in VOB format may be encrypted.
Windows Media DRM or WMDRM, is a Digital Rights Management service for the Windows Media platform. It is designed to provide delivery of audio or video content over an IP network to a PC or other playback device in such a way that the distributor can control how that content is used.

Slyck.com was a website that produced unique original file sharing news stories, shared aggregated technology news stories from the World Wide Web, and had a user forum.
Broadcast encryption is the cryptographic problem of delivering encrypted content over a broadcast channel in such a way that only qualified users can decrypt the content. The challenge arises from the requirement that the set of qualified users can change in each broadcast emission, and therefore revocation of individual users or user groups should be possible using broadcast transmissions, only, and without affecting any remaining users. As efficient revocation is the primary objective of broadcast encryption, solutions are also referred to as revocation schemes.

RedFox is a software development company based in Belize. The company is most prominently known for its software AnyDVD, which can be used to bypass copy protection measures on optical media, including DVD and Blu-ray Disc media, as well as CloneCD, which is used to back up the contents of optical discs.

BackupHDDVD is a small computer software utility program available in command line and GUI versions which aids in the decryption of commercial HD DVD discs protected by the Advanced Access Content System. It is used to back up discs, often to enable playback on hardware configurations without full support for HDCP. The program's source code was posted online, but no licence information was given.
The Protected Media Path is a set of technologies creating a "Protected Environment," first included in Microsoft's Windows Vista operating system, that is used to enforce digital rights management protections on content. Its subsets are Protected Video Path (PVP) and Protected User Mode Audio (PUMA). Any application that uses Protected Media Path in Windows uses Media Foundation.

The Advanced Access Content System (AACS) is a standard for content distribution and digital rights management, intended to restrict access to and copying of the post-DVD generation of optical discs. The specification was publicly released in April 2005. The standard has been adopted as the access restriction scheme for HD DVD and Blu-ray Disc (BD). It is developed by AACS Licensing Administrator, LLC, a consortium that includes Disney, Intel, Microsoft, Panasonic, Warner Bros., IBM, Toshiba and Sony. AACS has been operating under an "interim agreement" since the final specification has not yet been finalized.

Digg, stylized in lowercase as digg, is an American news aggregator with a curated front page, aiming to select stories specifically for the Internet audience such as science, trending political issues, and viral Internet issues. It was launched in its current form on July 31, 2012, with support for sharing content to other social platforms such as Twitter and Facebook.
Doom9 is a website featuring information on digital audio and video manipulation and digital copyrights. It is also the forum username of the author of the page, an Austrian who was a college student at the time of the creation of the site. The site's tagline is "The Definitive DVD Backup Resource".

HD DVD is an obsolete high-density optical disc format for storing data and playback of high-definition video. Supported principally by Toshiba, HD DVD was envisioned to be the successor to the standard DVD format, but lost to Blu-ray, supported by Sony and others.
BD+ is a component of the Blu-ray Disc digital rights management system. It was developed by Cryptography Research Inc. and is based on their Self-Protecting Digital Content concept. Its intent was to prevent unauthorized copies of Blu-ray discs and the playback of Blu-ray media using unauthorized devices.

The Free Speech Flag is a symbol of personal liberty used to promote freedom of speech. Designed by artist John Marcotte, the flag and its colors correspond to a cryptographic key which enabled users to copy HD DVDs and Blu-ray Discs. It was created on May 1, 2007, during the AACS encryption key controversy.

The security of Advanced Access Content System (AACS) has been a subject of discussion amongst security researchers, high definition video enthusiasts, and consumers at large since its inception. A successor to Content Scramble System (CSS), the digital rights management mechanism used by commercial DVDs, AACS was intended to improve upon the design of CSS by addressing flaws which had led to the total circumvention of CSS in 1999. The AACS system relies on a subset difference tree combined with a certificate revocation mechanism to ensure the security of high definition video content in the event of a compromise.
The Content Scramble System (CSS) is a digital rights management (DRM) and encryption system employed on many commercially produced DVD-Video discs. CSS utilizes a proprietary 40-bit stream cipher algorithm. The system was introduced around 1996 and was first compromised in 1999.
The WIPO Copyright and Performances and Phonograms Treaties Implementation Act, is a part of the Digital Millennium Copyright Act (DMCA), a 1998 U.S. law. It has two major portions, Section 102, which implements the requirements of the WIPO Copyright Treaty, and Section 103, which arguably provides additional protection against the circumvention of copy prevention systems and prohibits the removal of copyright management information.
Digital rights management (DRM) is the management of legal access to digital content. Various tools or technological protection measures (TPM), such as access control technologies, can restrict the use of proprietary hardware and copyrighted works. DRM technologies govern the use, modification and distribution of copyrighted works and of systems that enforce these policies within devices. DRM technologies include licensing agreements and encryption.
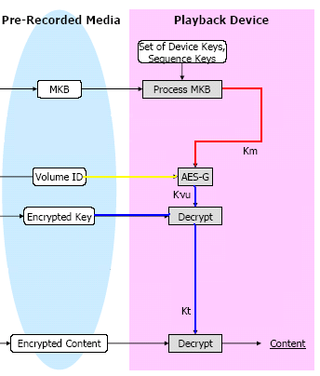
The Media Key Block (MKB) is one of the keys included inside the copying protection system (DRM) AACS. This system is used to prevent Blu-ray and HD DVD formats from being copied. The system was developed by companies from the film industry and the electronics industry including IBM, Intel, Microsoft, Matsushita (Panasonic), Sony, Toshiba, The Walt Disney Company and Warner Bros.
A user revolt is a social conflict in which users of a website collectively and openly protest a website host's or administrator's instructions for using the website. Sometimes it happens that the website hosts can control a website's use in certain ways, but the hosts also depend on the users to comply with voluntary social rules in order for the website to operate as the hosts would like. A user revolt occurs when the website users protest against the voluntary social rules of a website, and use the website in a way that is in conflict with the wishes of the website host or administrators.









