
In computing, BIOS is firmware used to provide runtime services for operating systems and programs and to perform hardware initialization during the booting process. The BIOS firmware comes pre-installed on an IBM PC or IBM PC compatible's system board and exists in some UEFI-based systems to maintain compatibility with operating systems that do not support UEFI native operation. The name originates from the Basic Input/Output System used in the CP/M operating system in 1975. The BIOS originally proprietary to the IBM PC has been reverse engineered by some companies looking to create compatible systems. The interface of that original system serves as a de facto standard.

A floppy disk or floppy diskette is a type of disk storage composed of a thin and flexible disk of a magnetic storage medium in a square or nearly square plastic enclosure lined with a fabric that removes dust particles from the spinning disk. Floppy disks store digital data which can be read and written when the disk is inserted into a floppy disk drive (FDD) connected to or inside a computer or other device.
Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types.

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
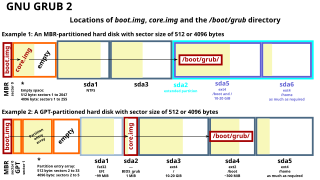
A boot sector is the sector of a persistent data storage device which contains machine code to be loaded into random-access memory (RAM) and then executed by a computer system's built-in firmware.
A boot disk is a removable digital data storage medium from which a computer can load and run (boot) an operating system or utility program. The computer must have a built-in program which will load and execute a program from a boot disk meeting certain standards.

CIH, also known as Chernobyl or Spacefiller, is a Microsoft Windows 9x computer virus that first emerged in 1998. Its payload is highly destructive to vulnerable systems, overwriting critical information on infected system drives and, in some cases, destroying the system BIOS. The virus was created by Chen Ing-hau, a student at Tatung University in Taiwan. It was believed to have infected sixty million computers internationally, resulting in an estimated NT$1 billion (US$35,801,231.56) in commercial damages.

Elk Cloner is one of the first known microcomputer viruses that spread "in the wild", i.e., outside the computer system or laboratory in which it was written. It attached itself to the Apple II operating system and spread by floppy disk. It was written around 1982 by programmer and entrepreneur Rich Skrenta as a 15-year-old high school student, originally as a joke, and put onto a game disk.

The Rainbow 100 is a microcomputer introduced by Digital Equipment Corporation (DEC) in 1982. This desktop unit had a monitor similar to the VT220 and a dual-CPU box with both 4 MHz Zilog Z80 and 4.81 MHz Intel 8088 CPUs. The Rainbow 100 was a triple-use machine: VT100 mode, 8-bit CP/M mode, and CP/M-86 or MS-DOS mode using the 8088. It ultimately failed to in the marketplace which became dominated by the simpler IBM PC and its clones which established the industry standard as compatibility with CP/M became less important than IBM PC compatibility. Writer David Ahl called it a disastrous foray into the personal computer market. The Rainbow was launched along with the similarly packaged DEC Professional and DECmate II which were also not successful. The failure of DEC to gain a significant foothold in the high-volume PC market would be the beginning of the end of the computer hardware industry in New England, as nearly all computer companies located there were focused on minicomputers for large organizations, from DEC to Data General, Wang, Prime, Computervision, Honeywell, and Symbolics Inc.
The Michelangelo virus is a computer virus first discovered on 4 February 1991 in Australia. The virus was designed to infect DOS systems, but did not engage the operating system or make any OS calls. Michelangelo, like all boot sector viruses, operated at the BIOS level. Each year, the virus remained dormant until March 6, the birthday of Renaissance artist Michelangelo. There is no reference to the artist in the virus, and it is doubtful that the virus's developer(s) intended a connection between the virus and the artist. The name was chosen by researchers who noticed the coincidence of the activation date. The actual significance of the date to the author is unknown. Michelangelo is a variant of the already endemic Stoned virus.
Distribution Media Format (DMF) is a format for floppy disks that Microsoft used to distribute software. It allowed the disk to contain 1680 KiB of data on a 31⁄2-inch disk, instead of the standard 1440 KiB. As a side effect, utilities had to specially support the format in order to read and write the disks, which made copying of products distributed on this medium more difficult. An Apple Macintosh computer running Disk Copy 6.3.3 on the Mac OS 7.6 or later operating system can copy and make DMF disks. The first Microsoft software product that uses DMF for distribution were the "c" revisions of Office 4.x. It also was the first software product to use CAB files, then called "Diamond".
Jerusalem is a logic bomb DOS virus first detected at Hebrew University of Jerusalem, in October 1987. On infection, the Jerusalem virus becomes memory resident, and then infects every executable file run, except for COMMAND.COM. COM files grow by 1,813 bytes when infected by Jerusalem and are not re-infected. Executable files grow by 1,808 to 1,823 bytes each time they are infected, and are then re-infected each time the files are loaded until they are too large to load into memory. Some .EXE files are infected but do not grow because several overlays follow the genuine .EXE file in the same file. Sometimes .EXE files are incorrectly infected, causing the program to fail to run as soon as it is executed.

The Disk II Floppy Disk Subsystem, often rendered as Disk ][, is a 5 +1⁄4-inch floppy disk drive designed by Steve Wozniak at the recommendation of Mike Markkula, and manufactured by Apple Computer, Inc. It went on sale in June 1978 at a retail price of US$495 for pre-order; it was later sold for $595 including the controller card and cable. The Disk II was designed specifically for use with the Apple II personal computer family to replace the slower cassette tape storage.

Stoned is a boot sector computer virus created in 1987. It is one of the first viruses and is thought to have been written by a student in Wellington, New Zealand. By 1989 it had spread widely in New Zealand and Australia, and variants became very common worldwide in the early 1990s.

The Ping-Pong virus is a boot sector virus discovered on March 1, 1988, at the Politecnico di Torino in Italy. It was likely the most common and best known boot sector virus until outnumbered by the Stoned virus.
A self-booting disk is a floppy disk for home computers or personal computers that loads—or boots—directly into a standalone application when the system is turned on, bypassing the operating system. This was common, even standard, on some computers in the late 1970s to early 1990s. Video games were the type of application most commonly distributed using this technique.

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.

The Macintosh External Disk Drive is the original model in a series of external 3+1⁄2-inch floppy disk drives manufactured and sold by Apple Computer exclusively for the Macintosh series of computers introduced in January 1984. Later, Apple would unify their external drives to work cross-platform between the Macintosh and Apple II product lines, dropping the name "Macintosh" from the drives. Though Apple had been producing external floppy disk drives prior to 1984, they were exclusively developed for the Apple II, III and Lisa computers using the industry standard 5+1⁄4-inch flexible disk format. The Macintosh external drives were the first to widely introduce Sony's new 3+1⁄2-inch rigid disk standard commercially and throughout their product line. Apple produced only one external 3+1⁄2-inch drive exclusively for use with the Apple II series called the Apple UniDisk 3.5.

Mikko Hermanni Hyppönen is a Finnish computer security expert, speaker and author. He is known for the Hyppönen Law about IoT security, which states that whenever an appliance is described as being "smart", it is vulnerable. He works as the Chief Research Officer at WithSecure and as the Principal Research Advisor at F-Secure.
The IBM Personal Computer Basic, commonly shortened to IBM BASIC, is a programming language first released by IBM with the IBM Personal Computer, Model 5150 in 1981. IBM released four different versions of the Microsoft BASIC interpreter, licensed from Microsoft for the PC and PCjr. They are known as Cassette BASIC, Disk BASIC, Advanced BASIC (BASICA), and Cartridge BASIC. Versions of Disk BASIC and Advanced BASIC were included with IBM PC DOS up to PC DOS 4. In addition to the features of an ANSI standard BASIC, the IBM versions offered support for the graphics and sound hardware of the IBM PC line. Source code could be entered with a full-screen editor, and limited facilities were provided for rudimentary program debugging. IBM also released a version of the Microsoft BASIC compiler for the PC concurrently with the release of PC DOS 1.10 in 1982.













