| Part of a series on |
| Global surveillance |
|---|
 |
| Disclosures |
| Systems |
| Agencies |
| Places |
| Laws |
| Proposed changes |
| Concepts |
| Related topics |
Fog Reveal is a tracking tool that aggregates location data from mobile apps. It is a product of FOG Data Science.
| Part of a series on |
| Global surveillance |
|---|
 |
| Disclosures |
| Systems |
| Agencies |
| Places |
| Laws |
| Proposed changes |
| Concepts |
| Related topics |
Fog Reveal is a tracking tool that aggregates location data from mobile apps. It is a product of FOG Data Science.
FOG Data Science is a limited liability company based in Virginia. It was founded in 2016 by two former United States Department of Homeland Security officials. Matthew Broderick, managing partner at the company, was director of operations for the DHS from 2005 to 2006. [1] [2]
FOG Data Science purchases commercially available location data from Virginia-based company Venntel, [3] collected from hundreds of mobile apps that sell information on user interests and movements, including the apps of Starbucks and Waze. [3] The information is derived from advertising IDs, unique user IDs assigned to mobile devices allowing advertisers to track people's movements, habits, and usage of apps. [1] [2] [4] [5] [6] Subscriptions to the service cost at least $7,500 per year. While the data is anonymized, officials have commented that competent law enforcement could use the information to identify individuals. According to FOG Data Science partner Matthew Broderick, their historical data profiles go back three years. [1]
Fog Reveal is used by local, state and federal law enforcement agencies in the United States, since at least 2018. Documents procured by the Electronic Frontier Foundation through the Freedom of Information Act revealed that FOG Data Science had 40 contracts with "nearly two dozen agencies," including the Dallas Police Department and the Rockingham County, North Carolina sheriff's office. [1] The software has been used to track individuals without requiring a search warrant. [7]
According to a 2022 Associated Press investigation supported by the Pulitzer Center on Crisis Reporting, law enforcement agencies used Fog Reveal "to search hundreds of billions of records from 250 million mobile devices, and harnessed the data to create location analyses known among law enforcement as 'patterns of life.'" [1] [8]
Privacy advocates raised concerns that the use of Fog Reveal by law enforcement agencies could constitute an unreasonable search and seizure, violating the Fourth Amendment to the United States Constitution. Electronic Frontier Foundation adviser Bennett Cyphers described the software as "sort of a mass surveillance program on a budget." [1]

Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception.
Telephone tapping is the monitoring of telephone and Internet-based conversations by a third party, often by covert means. The wire tap received its name because, historically, the monitoring connection was an actual electrical tap on the telephone line. Legal wiretapping by a government agency is also called lawful interception. Passive wiretapping monitors or records the traffic, while active wiretapping alters or otherwise affects it.
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored.

Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, such as organizations like the NSA, but it may also be carried out by corporations. Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is also often distinguished from targeted surveillance.
Harris Corporation was an American technology company, defense contractor, and information technology services provider that produced wireless equipment, tactical radios, electronic systems, night vision equipment and both terrestrial and spaceborne antennas for use in the government, defense and commercial sectors. They specialized in surveillance solutions, microwave weaponry, and electronic warfare. In 2019, it merged with L3 Technologies to form L3Harris Technologies.

Mobile phone tracking is a process for identifying the location of a mobile phone, whether stationary or moving. Localization may be effected by a number of technologies, such as the multilateration of radio signals between (several) cell towers of the network and the phone or by simply using GNSS. To locate a mobile phone using multilateration of mobile radio signals, the phone must emit at least the idle signal to contact nearby antenna towers and does not require an active call. The Global System for Mobile Communications (GSM) is based on the phone's signal strength to nearby antenna masts.
An international mobile subscriber identity-catcher, or IMSI-catcher, is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking location data of mobile phone users. Essentially a "fake" mobile tower acting between the target mobile phone and the service provider's real towers, it is considered a man-in-the-middle (MITM) attack. The 3G wireless standard offers some risk mitigation due to mutual authentication required from both the handset and the network. However, sophisticated attacks may be able to downgrade 3G and LTE to non-LTE network services which do not require mutual authentication.
A GPS tracking unit, geotracking unit, satellite tracking unit, or simply tracker is a navigation device normally on a vehicle, asset, person or animal that uses satellite navigation to determine its movement and determine its WGS84 UTM geographic position (geotracking) to determine its location. Satellite tracking devices send special satellite signals that are processed by a receiver.
Employee monitoring software is a means of employee monitoring, and allows company administrators to monitor and supervise all their employee computers from a central location. It is normally deployed over a business network and allows for easy centralized log viewing via one central networked PC. Sometimes, companies opt to monitor their employees using remote desktop software instead.
Cellebrite is an Israeli digital intelligence company that provides tools for federal, state, and local law enforcement as well as enterprise companies and service providers to collect, review, analyze and manage digital data. On April 8, 2021, Cellebrite announced plans to go public via a merger with a blank-check firm, valuing the company at approximately $2.4 billion. Their flagship product series is the Cellebrite UFED.

The StingRay is an IMSI-catcher, a cellular phone surveillance device, manufactured by Harris Corporation. Initially developed for the military and intelligence community, the StingRay and similar Harris devices are in widespread use by local and state law enforcement agencies across Canada, the United States, and in the United Kingdom. Stingray has also become a generic name to describe these kinds of devices.
The Geolocation Privacy and Surveillance Act was a bill introduced in the U.S. Congress in 2011 that attempted to limit government surveillance using geolocation information such as signals from GPS systems in mobile devices. The bill was sponsored by Sen. Ron Wyden and Rep. Jason Chaffetz. Since its initial proposal in June 2011, the GPS Act awaits consideration by the Senate Judiciary Committee as well as the House.

Ring LLC is a home security and smart home company owned by Amazon. Ring manufactures home security products that incorporate outdoor surveillance cameras, including the Ring Video Doorbell smart doorbell, and hosts an app, Neighbors, for online social sharing of captured footage among users. Ring also provides video footage from its cameras and data from its Neighbors app to law enforcement agencies on request. Its police partnerships have been criticized by civil rights advocacy groups as building an invasive private surveillance network. Privacy concerns have increased since Mayor London Breed of San Francisco has supported ordinances that would allow city police to be able to access Ring footage at any time.

The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveillance continued throughout the Cold War period, via programs such as the Black Chamber and Project SHAMROCK. The formation and growth of federal law-enforcement and intelligence agencies such as the FBI, CIA, and NSA institutionalized surveillance used to also silence political dissent, as evidenced by COINTELPRO projects which targeted various organizations and individuals. During the Civil Rights Movement era, many individuals put under surveillance orders were first labelled as integrationists, then deemed subversive, and sometimes suspected to be supportive of the communist model of the United States' rival at the time, the Soviet Union. Other targeted individuals and groups included Native American activists, African American and Chicano liberation movement activists, and anti-war protesters.

In re Application of the United States for Historical Cell Site Data, 724 F.3d 600, was a case in which the United States Court of Appeals for the Fifth Circuit held that the government can access cell site records without a warrant. Specifically, the court held that court orders under the Stored Communications Act compelling cell phone providers to disclose historical cell site information are not per se unconstitutional.
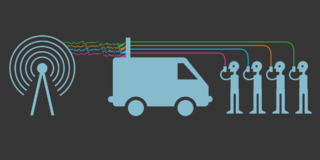
Cellphone surveillance may involve tracking, bugging, monitoring, eavesdropping, and recording conversations and text messages on mobile phones. It also encompasses the monitoring of people's movements, which can be tracked using mobile phone signals when phones are turned on.
Carpenter v. United States, 138 S.Ct. 2206 (2018), is a landmark United States Supreme Court case concerning the privacy of historical cell site location information (CSLI). The Court held that the government violates the Fourth Amendment to the United States Constitution when it accesses historical CSLI records containing the physical locations of cellphones without a search warrant.
Clearview AI is an American facial recognition company, providing software to companies, law enforcement, universities, and individuals. The company's algorithm matches faces to a database of more than 20 billion images indexed from the Internet, including social media applications. Founded by Hoan Ton-That and Richard Schwartz, the company maintained a low profile until late 2019, when its usage by law enforcement was reported on. Multiple reports identified Clearview's association with far-right personas dating back to 2016, when the company claimed to sever ties with two employees.

Hyper surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens that specifically utilizes technology and security breaches to access information. As the reliance on the internet economy grows, smarter technology with higher surveillance concerns and snooping means workers to have increased surveillance at their workplace. Hyper surveillance is highly targeted and intricate observation and monitoring among an individual, group of people, or faction.
A reverse search warrant is a type of search warrant used in the United States, in which law enforcement obtains a court order for information from technology companies to identify a group of people who may be suspects in a crime. They differ from traditional search warrants, which typically apply to specific individuals. Geo-fence warrants, which seek data on mobile phone users who were in a specific location at a given time, and keyword warrants, which request information on users who searched specific phrases, are two types of reverse search warrants.