The international mobile subscriber identity (IMSI) is a number that uniquely identifies every user of a cellular network. It is stored as a 64-bit field and is sent by the mobile device to the network. It is also used for acquiring other details of the mobile in the home location register (HLR) or as locally copied in the visitor location register. To prevent eavesdroppers from identifying and tracking the subscriber on the radio interface, the IMSI is sent as rarely as possible and a randomly-generated TMSI is sent instead.

A SIM card is an integrated circuit (IC) intended to securely store the international mobile subscriber identity (IMSI) number and its related key, which are used to identify and authenticate subscribers on mobile telephony devices. Technically the actual physical card is known as a universal integrated circuit card (UICC); this smart card is usually made of PVC with embedded contacts and semiconductors, with the SIM as its primary component. In practise the term "SIM card" refers to the entire unit and not simply the IC.
A SIM lock, simlock, network lock, carrier lock or (master) subsidy lock is a technical restriction built into GSM and CDMA mobile phones by mobile phone manufacturers for use by service providers to restrict the use of these phones to specific countries and/or networks. This is in contrast to a phone that does not impose any SIM restrictions.

Near-field communication (NFC) is a set of communication protocols that enables communication between two electronic devices over a distance of 4 cm (1.57 in) or less. NFC offers a low-speed connection through a simple setup that can be used to bootstrap more capable wireless connections. Like other "proximity card" technologies, NFC is based on inductive coupling between two so-called antennas present on NFC-enabled devices—for example a smartphone and a printer—communicating in one or both directions, using a frequency of 13.56 MHz in the globally available unlicensed radio frequency ISM band using the ISO/IEC 18000-3 air interface standard at data rates ranging from 106 to 424 kbit/s.

The International Mobile Equipment Identity (IMEI) is a numeric identifier, usually unique, for 3GPP and iDEN mobile phones, as well as some satellite phones. It is usually found printed inside the battery compartment of the phone but can also be displayed on-screen on most phones by entering *#06# MMI Supplementary Service code on the dialpad, or alongside other system information in the settings menu on smartphone operating systems.
The Open Mobile Terminal Platform (OMTP) was a forum created by mobile network operators to discuss standards with manufacturers of mobile phones and other mobile devices. During its lifetime, the OMTP included manufacturers such as Huawei, LG Electronics, Motorola, Nokia, Samsung and Sony Ericsson.

Cloud9 is a mobile network operator focussed on providing mobile subscriptions over the air to programmable SIM cards, SoftSIMs and eSIMs. Their service is used in both smartphones and IoT devices.
Mobile device management (MDM) is the administration of mobile devices, such as smartphones, tablet computers, and laptops. MDM is usually implemented with the use of a third-party product that has management features for particular vendors of mobile devices. Though closely related to Enterprise Mobility Management and Unified Endpoint Management, MDM differs slightly from both: unlike MDM, EMM includes mobile information management, BYOD, mobile application management and mobile content management, whereas UEM provides device management for endpoints like desktops, printers, IoT devices, and wearables as well.
Rich Communication Services (RCS) is a communication protocol between mobile telephone carriers and between phone and carrier, aiming at replacing SMS messages with a text-message system that is richer, provides phonebook polling, and can transmit in-call multimedia. It is part of the broader IP Multimedia Subsystem. Google added support for end-to-end encryption for all chats in their own RCS-based app, Messages.
A CDMA subscriber identity module (CSIM) is an application to support CDMA2000 phones that runs on a UICC, with a file structure derived from the R-UIM card. By porting the application to the UICC, a card with CSIM, SIM, and USIM can operate with all major cellular technologies worldwide. The CSIM application allows users to change phones by simply removing the smart card from one mobile phone and inserting it into another mobile phone or broadband telephony device supporting the CDMA2000 radio interface.
MIFARE4Mobile is a technical specification published by NXP Semiconductors in December 2008 to manage MIFARE-based applications in mobile devices. The specification provides mobile network operators and service providers with a single, interoperable programming interface, easing the use of the contactless MIFARE technology in future mobile Near Field Communication (NFC) devices.
The (U)SIM interface is the connecting point of the mobile phone and the UICC with its SIM or USIM application.
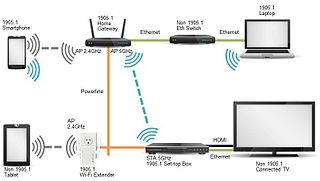
IEEE 1905.1 is an IEEE standard which defines a network enabler for home networking supporting both wireless and wireline technologies: IEEE 802.11, IEEE 1901 powerline networking, IEEE 802.3 Ethernet and Multimedia over Coax (MoCA).
In cryptography, a Key Checksum Value (KCV) is the checksum of a cryptographic key. It is used to validate the key integrity or compare keys without knowing their actual values. The KCV is computed by encrypting a block of bytes, each with value '00' or '01', with the cryptographic key and retaining the first 6 hexadecimal characters of the encrypted result. It is used in key management in different ciphering devices, like SIM-cards or Hardware Security Modules (HSM).
Apple SIM is a proprietary subscriber identity module (SIM) produced by Apple Inc. It is included in GPS + Cellular versions of iPad Air 2 and later, iPad mini 3 and later, and iPad Pro.
An eSIM (embedded-SIM) is a form of SIM card that is embedded directly into a device. Instead of an integrated circuit located on a removable universal integrated circuit card (UICC), typically made of PVC, an eSIM consists of software installed onto an eUICC chip permanently attached to a device. If the eSIM is eUICC compatible, it can be re-programmed with new SIM information. Otherwise, the eSIM is programmed with it's ICCID/IMSI and other information at the time it is manufactured, and cannot be changed.

ASPIDER is the group name for a series of companies that are mostly based in Europe. The company name has evolved over the years as a result of acquisitions, mergers and restructuring. The company is an MVNE, providing mobile services to companies that want to control their own network. Clients include enterprises, manufacturers, integrators, and the mobile operators themselves.
Simjacker is a cellular software exploit for SIM Cards discovered by AdaptiveMobile Security. 29 countries are vulnerable according to ZDNet. The vulnerability has been exploited primarily in Mexico, but also Colombia and Peru, according to the Wall Street Journal, where it was used to track the location of mobile phone users without their knowledge.
A secure element (SE) is a secure operating system (OS) in a tamper-resistant processor chip or secure component. It can protect assets (root of trust, sensitive data, keys, certificates, applications) against high level software and hardware attacks. Applications that process this sensitive data on an SE are isolated and so operate within a controlled environment not impacted by software (including possible malware) found elsewhere on the OS.
eUICC refers to the architectural standards published by the GSM Association (GSMA) or implementations of those standard for eSIM, a device used to securely store one or more SIM card profiles, which are the unique identifiers and cryptographic keys used by cellular network service providers to uniquely identify and securely connect to mobile network devices. Applications of eUICC are found in mobile network devices that use GSM cellular network eSIM technology.





