
Pidgin is a free and open-source multi-platform instant messaging client, based on a library named libpurple that has support for many instant messaging protocols, allowing the user to simultaneously log in to various services from a single application, with a single interface for both popular and obsolete protocols, thus avoiding the hassle of having to deal with new software for each device and protocol.
Skype is a proprietary telecommunications application operated by Skype Technologies, a division of Microsoft, best known for VoIP-based videotelephony, videoconferencing and voice calls. It also has instant messaging, file transfer, debit-based calls to landline and mobile telephones, and other features. It is available on various desktop, mobile, and video game console platforms.
End-to-end encryption (E2EE) is a private communication system in which only communicating users can participate. As such, no one, including the communication system provider, telecom providers, Internet providers or malicious actors, can access the cryptographic keys needed to converse.
The following is a comparison of instant messaging protocols. It contains basic general information about the protocols.
Off-the-record Messaging (OTR) is a cryptographic protocol that provides encryption for instant messaging conversations. OTR uses a combination of AES symmetric-key algorithm with 128 bits key length, the Diffie–Hellman key exchange with 1536 bits group size, and the SHA-1 hash function. In addition to authentication and encryption, OTR provides forward secrecy and malleable encryption.
Protocol encryption (PE), message stream encryption (MSE) or protocol header encrypt (PHE) are related features of some peer-to-peer file-sharing clients, including BitTorrent clients. They attempt to enhance privacy and confidentiality. In addition, they attempt to make traffic harder to identify by third parties including internet service providers (ISPs). However, encryption will not protect one from DMCA notices from sharing not legal content, as one is still uploading material and the monitoring firms can merely connect to the swarm.
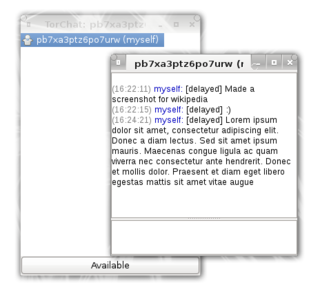
TorChat was a peer-to-peer anonymous instant messenger that used Tor onion services as its underlying network. It provided cryptographically secure text messaging and file transfers. The characteristics of Tor's onion services ensure that all traffic between the clients is encrypted and that it is very difficult to tell who is communicating with whom and where a given client is physically located.

Jami is a SIP-compatible distributed peer-to-peer softphone and SIP-based instant messenger for Linux, Microsoft Windows, macOS, iOS, and Android. Jami was developed and maintained by the Canadian company Savoir-faire Linux, and with the help of a global community of users and contributors, Jami positions itself as a potential free Skype replacement.

Cryptocat is a discontinued open-source desktop application intended to allow encrypted online chatting available for Windows, OS X, and Linux. It uses end-to-end encryption to secure all communications to other Cryptocat users. Users are given the option of independently verifying their buddies' device lists and are notified when a buddy's device list is modified and all updates are verified through the built-in update downloader.

Twister is a decentralized, experimental peer-to-peer microblogging program which uses end-to-end encryption to safeguard communications. Based on BitTorrent- and Bitcoin-like protocols, it has been likened to a distributed version of Twitter.
TextSecure was an encrypted messaging application for Android that was developed from 2010 to 2015. It was a predecessor to Signal and the first application to use the Signal Protocol, which has since been implemented into WhatsApp and other applications. TextSecure used end-to-end encryption to secure the transmission of text messages, group messages, attachments and media messages to other TextSecure users.

Ricochet or Ricochet IM is a free software, multi-platform, instant messaging software project originally developed by John Brooks and later adopted as the official instant messaging client project of the Invisible.im group. A goal of the Invisible.im group is to help people maintain privacy by developing a "metadata free" instant messaging client.

Matrix is an open standard and communication protocol for real-time communication. It aims to make real-time communication work seamlessly between different service providers, in the way that standard Simple Mail Transfer Protocol email currently does for store-and-forward email service, by allowing users with accounts at one communications service provider to communicate with users of a different service provider via online chat, voice over IP, and videotelephony. It therefore serves a similar purpose to protocols like XMPP, but is not based on any existing communication protocol.

OMEMO is an extension to the Extensible Messaging and Presence Protocol (XMPP) for multi-client end-to-end encryption developed by Andreas Straub. According to Straub, OMEMO uses the Double Ratchet Algorithm "to provide multi-end to multi-end encryption, allowing messages to be synchronized securely across multiple clients, even if some of them are offline". The name "OMEMO" is a recursive acronym for "OMEMO Multi-End Message and Object Encryption". It is an open standard based on the Double Ratchet Algorithm and the Personal Eventing Protocol . OMEMO offers future and forward secrecy and deniability with message synchronization and offline delivery.
In cryptography, the Double Ratchet Algorithm is a key management algorithm that was developed by Trevor Perrin and Moxie Marlinspike in 2013. It can be used as part of a cryptographic protocol to provide end-to-end encryption for instant messaging. After an initial key exchange it manages the ongoing renewal and maintenance of short-lived session keys. It combines a cryptographic so-called "ratchet" based on the Diffie–Hellman key exchange (DH) and a ratchet based on a key derivation function (KDF), such as a hash function, and is therefore called a double ratchet.
The Signal Protocol is a non-federated cryptographic protocol that provides end-to-end encryption for voice and instant messaging conversations. The protocol was developed by Open Whisper Systems in 2013 and was first introduced in the open-source TextSecure app, which later became Signal. Several closed-source applications have implemented the protocol, such as WhatsApp, which is said to encrypt the conversations of "more than a billion people worldwide" or Google who provides end-to-end encryption by default to all RCS-based conversations between users of their Google Messages app for one-to-one conversations. Facebook Messenger also say they offer the protocol for optional Secret Conversations, as does Skype for its Private Conversations.
Wire is an encrypted communication and collaboration app created by Wire Swiss. It is available for iOS, Android, Windows, macOS, Linux, and web browsers such as Firefox. Wire offers a collaboration suite featuring messenger, voice calls, video calls, conference calls, file-sharing, and external collaboration – all protected by a secure end-to-end-encryption. Wire offers three solutions built on its security technology: Wire Pro – which offers Wire's collaboration feature for businesses, Wire Enterprise – includes Wire Pro capabilities with added features for large-scale or regulated organizations, and Wire Red – the on-demand crisis collaboration suite. They also offer Wire Personal, which is a secure messaging app for personal use.
Autocrypt is a cryptographic protocol for email clients aiming to simplify key exchange and enabling encryption. Version 1.0 of the Autocrypt specification was released in December 2017 and makes no attempt to protect against MITM attacks. It is implemented on top of OpenPGP replacing its complex key management by fully automated exchange of cryptographic keys between peers.

Secure Scuttlebutt (SSB) is a peer-to peer communication protocol, mesh network, and self-hosted social media ecosystem. Each user hosts their own content and the content of the peers they follow, which provides fault tolerance and eventual consistency. Messages are digitally signed and added to an append-only list of messages published by an author. SSB is primarily used for implementing distributed social networks, and utilizes cryptography to assure that content remains unforged as it is propagated through the network.

Conversations is a free software, instant messaging client application software for Android. It is largely based on recognized open standards such as the Extensible Messaging and Presence Protocol (XMPP) and Transport Layer Security (TLS).











