- English Language Reward Poster for Pavel Aleksandrovich Akulov, Mikhail Mikhailovich Gavrilov, and Marat Valeryevich Tyukov
- Russian Language Reward Poster for Pavel Aleksandrovich Akulov, Mikhail Mikhailovich Gavrilov, and Marat Valeryevich Tyukov
- English Language Reward Poster for Evgeny Viktorovich Gladkikh
- Russian Language Reward Poster for Evgeny Viktorovich Gladkikh
Related Research Articles

Information warfare (IW) is the battlespace use and management of information and communication technology (ICT) in pursuit of a competitive advantage over an opponent. It is different from cyberwarfare that attacks computers, software, and command control systems. Information warfare is the manipulation of information trusted by a target without the target's awareness so that the target will make decisions against their interest but in the interest of the one conducting information warfare. As a result, it is not clear when information warfare begins, ends, and how strong or destructive it is.

The Main Directorate of the General Staff of the Armed Forces of the Russian Federation, formerly the Main Intelligence Directorate, and still commonly known by its previous abbreviation GRU, is the foreign military intelligence agency of the General Staff of the Armed Forces of the Russian Federation. The GRU controls the military intelligence service and maintains its own special forces units.

The Federal Security Service of the Russian Federation is the principal security agency of Russia and the main successor agency to the Soviet Union's KGB; its immediate predecessor was the Federal Counterintelligence Service (FSK) which was reorganized into the FSB in 1995. The three major structural successor components of the former KGB that remain administratively independent of the FSB are the Foreign Intelligence Service (SVR), the Federal Protective Service (FSO), and the Main Directorate of Special Programs of the President of the Russian Federation (GUSP).

Konstantin Igorevich Rykov, a.k.a. Jason Foris is a Russian politician.
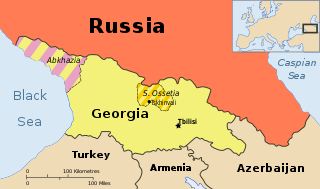
During the Russo-Georgian War, a series of cyberattacks swamped and disabled websites of numerous South Ossetian, Georgian, Russian and Azerbaijani organisations. The attacks were initiated three weeks before the shooting war began.
Cyberwarfare by Russia includes denial of service attacks, hacker attacks, dissemination of disinformation and propaganda, participation of state-sponsored teams in political blogs, internet surveillance using SORM technology, persecution of cyber-dissidents and other active measures. According to investigative journalist Andrei Soldatov, some of these activities were coordinated by the Russian signals intelligence, which was part of the FSB and formerly a part of the 16th KGB department. An analysis by the Defense Intelligence Agency in 2017 outlines Russia's view of "Information Countermeasures" or IPb as "strategically decisive and critically important to control its domestic populace and influence adversary states", dividing 'Information Countermeasures' into two categories of "Informational-Technical" and "Informational-Psychological" groups. The former encompasses network operations relating to defense, attack, and exploitation and the latter to "attempts to change people's behavior or beliefs in favor of Russian governmental objectives."

The United States has often accused the People's Republic of China of attempting to unlawfully acquire U.S. military technology and classified information as well as trade secrets of U.S. companies in order to support China's long-term military and commercial development. Chinese government agencies and affiliated personnel have been accused of using a number of methods to obtain U.S. technology, including espionage, exploitation of commercial entities, and a network of scientific, academic and business contacts. Prominent espionage cases include Larry Wu-tai Chin, Katrina Leung, Gwo-Bao Min, Chi Mak and Peter Lee. The Ministry of State Security (MSS) maintains a bureau dedicated to espionage against the United States, the United States Bureau.
Cyberwarfare is the use of computer technology to disrupt the activities of a state or organization, especially the deliberate attacking of information systems for strategic or military purposes. As a major developed economy, the United States is highly dependent on the Internet and therefore greatly exposed to cyber attacks. At the same time, the United States has substantial capabilities in both defense and power projection thanks to comparatively advanced technology and a large military budget. Cyber warfare presents a growing threat to physical systems and infrastructures that are linked to the internet. Malicious hacking from domestic or foreign enemies remains a constant threat to the United States. In response to these growing threats, the United States has developed significant cyber capabilities.
Cyberwarfare by China is the aggregate of all combative activities in the cyberspace which are taken by organs of the People's Republic of China, including affiliated advanced persistent threat (APT) groups, against other countries.
A cyberattack is any offensive maneuver that targets computer information systems, computer networks, infrastructures, personal computer devices, or smartphones. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Depending on the context, cyberattacks can be part of cyber warfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, societies or organizations and it may originate from an anonymous source. A product that facilitates a cyberattack is sometimes called a cyber weapon. Cyberattacks have increased over the last few years. A well-known example of a cyberattack is a distributed denial of service attack.

PLA Unit 61398 is the Military Unit Cover Designator (MUCD) of a People's Liberation Army advanced persistent threat unit that has been alleged to be a source of Chinese computer hacking attacks. The unit is stationed in Pudong, Shanghai, and has been cited by US intelligence agencies since 2002.
PLA Unit 61486 is a People's Liberation Army unit dedicated to cyberattacks on American, Japanese, and European corporations focused on satellite and communications technology. It is a unit that takes part in China's campaign to steal trade and military secrets from foreign targets.
Cozy Bear, classified by the United States federal government as advanced persistent threat APT29, is a Russian hacker group believed to be associated with one or more intelligence agencies of Russia. The Dutch General Intelligence and Security Service (AIVD) deduced from security camera footage that it is led by the Russian Foreign Intelligence Service (SVR), a view shared by the United States. Cybersecurity firm CrowdStrike also previously suggested that it may be associated with either the Russian Federal Security Service (FSB) or SVR. The group has been given various nicknames by other cybersecurity firms, including CozyCar, CozyDuke, Dark Halo, The Dukes, Midnight Blizzard, NOBELIUM, Office Monkeys, StellarParticle, UNC2452, and YTTRIUM.
Fancy Bear, also known as APT28, Pawn Storm, Sofacy Group, Sednit, Tsar Team and STRONTIUM or Forest Blizzard, is a Russian cyber espionage group. Cybersecurity firm CrowdStrike has said with a medium level of confidence that it is associated with the Russian military intelligence agency GRU. The UK's Foreign and Commonwealth Office as well as security firms SecureWorks, ThreatConnect, and Mandiant, have also said the group is sponsored by the Russian government. In 2018, an indictment by the United States Special Counsel identified Fancy Bear as GRU Unit 26165. This refers to its unified Military Unit Number of the Russian army regiments. The headquarters of Fancy Bear and the entire military unit, which reportedly specializes in state-sponsored cyberattacks and decryption of hacked data, were targeted by Ukrainian drones on July 24, 2023, the rooftop on an adjacent building collapsed as a result of the explosion.

DCLeaks was a website that was established in June 2016. It was responsible for publishing leaks of emails belonging to multiple prominent figures in the United States government and military. Cybersecurity research firms determined the site is a front for the Russian cyber-espionage group Fancy Bear. On July 13, 2018, an indictment was made against 12 Russian GRU military officers; it alleged that DCLeaks is part of a Russian military operation to interfere in the 2016 U.S. presidential election.

A.F. Mozhaysky's Military-Space Academy is a Military Academy of the Armed Forces of the Russian Federation. It is located in Saint Petersburg. It is associated with the Russian Aerospace Defence Forces.

The Plot to Hack America: How Putin's Cyberspies and WikiLeaks Tried to Steal the 2016 Election is a non-fiction book by Malcolm Nance about the Russian interference in the 2016 United States elections. It was published in paperback, audiobook, and e-book formats in 2016 by Skyhorse Publishing. A second edition was also published the same year, and a third edition in 2017. Nance researched Russian intelligence, working as a Russian interpreter and studying KGB history.

Yevgeniy Alexandrovich Nikulin is a Russian computer hacker. He was arrested in Prague in October 2016, and was charged with the hacking and data theft of several U.S. technology companies. In September 2020, he was sentenced to 88 months in prison.

Dmitry Aleksandrovich Dokuchaev is a Russian convicted cyber criminal and a former intelligence officer of the Federal Security Service (FSB), the principal security agency of Russia. In April 2019, he was sentenced to six years in prison for treason.

Sandworm is an advanced persistent threat operated by Military Unit 74455, a cyberwarfare unit of the GRU, Russia's military intelligence service. Other names for the group, given by cybersecurity researchers, include Telebots, Voodoo Bear, IRIDIUM, Seashell Blizzard, and Iron Viking.
References
- ↑ "Center 16" is the translation contained within the indictments. Elsewhere, the Estonian Foreign Intelligence Service refers to the unit as "16th Centre." see "International Security and Estonia 2019" (PDF). valisluureamet.ee. Estonian Foreign Intelligence Service. pp. 56–60. Archived (PDF) from the original on 9 March 2022. Retrieved 6 April 2022.
- 1 2 3 Greenberg, Andy. "The Russian Hackers Playing 'Chekhov's Gun' With US Infrastructure". Wired– via www.wired.com.
- ↑ "How Microsoft names threat actors". Microsoft. Retrieved 21 January 2024.
- ↑ "Dragonfly 2.0, IRON LIBERTY, DYMALLOY, Berserk Bear, Group G0074 | MITRE ATT&CK®". attack.mitre.org.
- 1 2 "Russian state hackers stole data from US government networks". BleepingComputer.
- ↑ Goodin, Dan (December 7, 2020). "NSA says Russian state hackers are using a VMware flaw to ransack networks". Ars Technica.
- 1 2 3 4 Bowen, Andrew S. (January 4, 2021). Russian Cyber Units (Report). Congressional Research Service. p. 2. Retrieved July 25, 2021.
- 1 2 "German intelligence agencies warn of Russian hacking threats to critical infrastructure". CyberScoop. May 26, 2020.
- ↑ Hvistendahl, Mara; Lee, Micah; Smith, Jordan (December 17, 2020). "Russian Hackers Have Been Inside Austin City Network for Months". The Intercept.
- ↑ "Austin officials quiet on reports that city network hacked". www.msn.com.
- ↑ "Indictment" (PDF), United States v. Gladkikh (Court Filing), no. 1:21-cr-00442, Docket 1, D.D.C., 26 Aug 2021, retrieved 5 April 2022– via Recap ( PACER current docket view
 )
) - ↑ "Russia's FSB malign activity: factsheet". gov.uk. Foreign, Commonwealth & Development Office. 5 April 2022. Retrieved 6 April 2022.
- 1 2 3 4 "Indictment" (PDF), United States v. Akulov, et al. (Court Filing), no. 1:21-cr-20047, Docket 3, D.K.S., 26 Aug 2021, retrieved 5 April 2022– via Recap ( PACER current docket view
 )
)



