Linux malware includes viruses, Trojans, worms and other types of malware that affect the Linux family of operating systems. Linux, Unix and other Unix-like computer operating systems are generally regarded as very well-protected against, but not immune to, computer viruses.

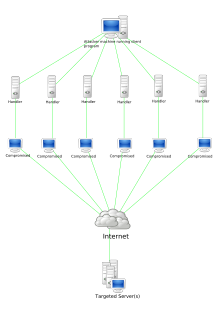
In computing, a zombie is a computer connected to the Internet that has been compromised by a hacker via a computer virus, computer worm, or trojan horse program and can be used to perform malicious tasks under the remote direction of the hacker. Zombie computers often coordinate together in a botnet controlled by the hacker, and are used for activities such as spreading e-mail spam and launching distributed denial-of-service attacks against web servers. Most victims are unaware that their computers have become zombies. The concept is similar to the zombie of Haitian Voodoo folklore, which refers to a corpse resurrected by a sorcerer via magic and enslaved to the sorcerer's commands, having no free will of its own. A coordinated DDoS attack by multiple botnet machines also resembles a "zombie horde attack", as depicted in fictional zombie films.
Internet security is a branch of computer security. It encompasses the Internet, browser security, web site security, and network security as it applies to other applications or operating systems as a whole. Its objective is to establish rules and measures to use against attacks over the Internet. The Internet is an inherently insecure channel for information exchange, with high risk of intrusion or fraud, such as phishing, online viruses, trojans, ransomware and worms.
Agobot, also frequently known as Gaobot, is a family of computer worms. Axel "Ago" Gembe, a German programmer also known for leaking Half-Life 2 a year before release, was responsible for writing the first version. The Agobot source code describes it as: “a modular IRC bot for Win32 / Linux”. Agobot was released under version 2 of the GNU General Public License. Agobot is a multi-threaded and mostly object oriented program written in C++ as well as a small amount of assembly. Agobot is an example of a Botnet that requires little or no programming knowledge to use.
Operation: Bot Roast is an operation by the FBI to track down bot herders, crackers, or virus coders who install malicious software on computers through the Internet without the owners' knowledge, which turns the computer into a zombie computer that then sends out spam to other computers from the compromised computer, making a botnet or network of bot infected computers. The operation was launched because the vast scale of botnet resources poses a threat to national security.

The Storm botnet or Storm worm botnet was a remotely controlled network of "zombie" computers that had been linked by the Storm Worm, a Trojan horse spread through e-mail spam. At its height in September 2007, the Storm botnet was running on anywhere from 1 million to 50 million computer systems, and accounted for 8% of all malware on Microsoft Windows computers. It was first identified around January 2007, having been distributed by email with subjects such as "230 dead as storm batters Europe," giving it its well-known name. The botnet began to decline in late 2007, and by mid-2008 had been reduced to infecting about 85,000 computers, far less than it had infected a year earlier.
Srizbi BotNet is considered one of the world's largest botnets, and responsible for sending out more than half of all the spam being sent by all the major botnets combined. The botnets consist of computers infected by the Srizbi trojan, which sent spam on command. Srizbi suffered a massive setback in November 2008 when hosting provider Janka Cartel was taken down; global spam volumes reduced up to 93% as a result of this action.
The Rustock botnet was a botnet that operated from around 2006 until March 2011.
The Cutwail botnet, founded around 2007, is a botnet mostly involved in sending spam e-mails. The bot is typically installed on infected machines by a Trojan component called Pushdo. It affects computers running Microsoft Windows.
The Bredolab botnet, also known by its alias Oficla, was a Russian botnet mostly involved in viral e-mail spam. Before the botnet was eventually dismantled in November 2010 through the seizure of its command and control servers, it was estimated to consist of millions of zombie computers.
United States of America v. Ancheta is the name of a lawsuit against Jeanson James Ancheta of Downey, California by the U.S. Government and was handled by the United States District Court for the Central District of California. This is the first botnet related prosecution in U.S history.
Slenfbot is the classification for a family of malicious software (malware), which infects files on Microsoft Windows systems. Slenfbot was first discovered in 2007 and, since then, numerous variants have followed; each with slightly different characteristics and new additions to the worm's payload, such as the ability to provide the attacker with unauthorized access to the compromised host. Slenfbot primarily spreads by luring users to follow links to websites, which contain a malicious payload. Slenfbot propagates via instant messaging applications, removable drives and/or the local network via network shares. The code for Slenfbot appears to be closely managed, which may provide attribution to a single group and/or indicate that a large portion of the code is shared amongst multiple groups. The inclusion of other malware families and variants as well as its own continuous evolution, makes Slenfbot a highly effective downloader with a propensity to cause even more damage to compromised systems.
ZeroAccess is a Trojan horse computer malware that affects Microsoft Windows operating systems. It is used to download other malware on an infected machine from a botnet while remaining hidden using rootkit techniques.
Festi is a rootkit and a botnet also known by its alias of Spamnost, and is mostly involved in email spam and denial of service attacks. It works under operating systems of the Windows family. Autumn of 2009 was the first time Festi came into the view of the companies engaged in the development and sale of antivirus software. At this time it was estimated that the botnet itself consisted of roughly 25.000 infected machines, while having a spam volume capacity of roughly 2.5 billion spam emails a day. Festi showed the greatest activity in 2011-2012. More recent estimates - dated August 2012 - display that the botnet is sending spam from 250,000 unique IP addresses, a quarter of the total amount of one million detected IP's sending spam mails. The main functionality of botnet Festi is spam sending and implementation of cyberattacks like "distributed denial of service".

The Microsoft Digital Crimes Unit (DCU) is a Microsoft sponsored team of international legal and internet security experts employing the latest tools and technologies to stop or interfere with cybercrime and cyber threats. The Microsoft Digital Crimes Unit was assembled in 2008. In 2013, a Cybercrime center for the DCU was opened in Redmond, Washington. There are about 100 members of the DCU stationed just in Redmond, Washington at the original Cybercrime Center. Members of the DCU include lawyers, data scientists, investigators, forensic analysts, and engineers. The DCU has international offices located in major cities such as: Beijing, Berlin, Bogota, Delhi, Dublin, Hong Kong, Sydney, and Washington, D.C. The DCU's main focuses are child protection, copyright infringement and malware crimes. The DCU must work closely with law enforcement to ensure the perpetrators are punished to the full extent of the law. The DCU has taken down many major botnets such as the Citadel, Rustock, and Zeus. Around the world malware has cost users about $113 billion and the DCU's jobs is to shut them down in accordance with the law.

GameOver ZeuS (GOZ), also known as peer-to-peer (P2P) ZeuS, ZeuS3, and GoZeus, is a Trojan horse developed by Russian cybercriminal Evgeniy Bogachev. Created in 2011 as a successor to Jabber Zeus, another project of Bogachev's, the malware is notorious for its usage in bank fraud resulting in damages of approximately $100 million and being the main vehicle through which the CryptoLocker ransomware attack was conducted, resulting in millions of dollars of losses. At the peak of its activity in 2012 and 2013, between 500,000 and 1 million computers were infected with GameOver ZeuS.
BASHLITE is malware which infects Linux systems in order to launch distributed denial-of-service attacks (DDoS). Originally it was also known under the name Bashdoor, but this term now refers to the exploit method used by the malware. It has been used to launch attacks of up to 400 Gbps.
Mirai is malware that turns networked devices running Linux into remotely controlled bots that can be used as part of a botnet in large-scale network attacks. It primarily targets online consumer devices such as IP cameras and home routers. The Mirai botnet was first found in August 2016 by MalwareMustDie, a white hat malware research group, and has been used in some of the largest and most disruptive distributed denial of service (DDoS) attacks, including an attack on 20 September 2016 on computer security journalist Brian Krebs' website, an attack on French web host OVH, and the October 2016 Dyn cyberattack. According to a chat log between Anna-senpai and Robert Coelho, Mirai was named after the 2011 TV anime series Mirai Nikki.
Remaiten is malware which infects Linux on embedded systems by brute forcing using frequently used default username and passwords combinations from a list in order to infect a system.
Code Shikara is a computer worm, related to the Dorkbot family, that attacks through social engineering.