Klez is a computer worm that propagates via e-mail. It first appeared in October 2001 and was originated in China. A number of variants of the worm exist.

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
The Melissa virus is a mass-mailing macro virus released on or around March 26, 1999. It targets Microsoft Word and Outlook-based systems and created considerable network traffic. The virus infects computers via email; the email is titled "Important Message From," followed by the current username. Upon clicking the message, the body reads, "Here's that document you asked for. Don't show anyone else ;)." Attached is a Word document titled "list.doc," containing a list of pornographic sites and accompanying logins for each. It then mass-mails itself to the first fifty people in the user's contact list and disables multiple safeguard features on Microsoft Word and Microsoft Outlook.

Blaster was a computer worm that spread on computers running operating systems Windows XP and Windows 2000 during August 2003.

Mydoom was a computer worm that targeted computers running Microsoft Windows. It was first sighted on January 26, 2004. It became the fastest-spreading e-mail worm ever, exceeding previous records set by the Sobig worm and ILOVEYOU, a record which as of 2024 has yet to be surpassed.
Bagle was a mass-mailing computer worm affecting Microsoft Windows. The first strain, Bagle.A, did not propagate widely. A second variant, Bagle.B, was considerably more virulent.
Agobot, also frequently known as Gaobot, is a family of computer worms. Axel "Ago" Gembe, a German programmer also known for leaking Half-Life 2 a year before release, was responsible for writing the first version. The Agobot source code describes it as: “a modular IRC bot for Win32 / Linux”. Agobot was released under version 2 of the GNU General Public License. Agobot is a multi-threaded and mostly object oriented program written in C++ as well as a small amount of assembly. Agobot is an example of a Botnet that requires little or no programming knowledge to use.
ILOVEYOU, sometimes referred to as the Love Bug or Loveletter, was a computer worm that infected over ten million Windows personal computers on and after May 5, 2000. It started spreading as an email message with the subject line "ILOVEYOU" and the attachment "LOVE-LETTER-FOR-YOU.TXT.vbs." At the time, Windows computers often hid the latter file extension by default because it is an extension for a file type that Windows knows, leading unwitting users to think it was a normal text file. Opening the attachment activates the Visual Basic script. First, the worm inflicts damage on the local machine, overwriting random files, then, it copies itself to all addresses in the Windows Address Book used by Microsoft Outlook, allowing it to spread much faster than any other previous email worm.
Zotob is a computer worm which exploits security vulnerabilities in Microsoft operating systems like Windows 2000, including the MS05-039 plug-and-play vulnerability. This worm has been known to spread on Microsoft-ds or TCP port 445.
The Sober worm is a family of computer worms that was discovered on October 24, 2003. Like many worms, Sober sends itself as an e-mail attachment, fake webpages, fake pop-up ads, and fake advertisements.
The Nimda virus is a malicious file-infecting computer worm. It quickly spread, surpassing the economic damage caused by previous outbreaks such as Code Red.
W32.Navidad is a mass-mailing worm program or virus, discovered in December 2000 that ran on Windows 95, Windows 98, Windows NT, and Windows 2000 systems. It was designed to spread through email clients such as Microsoft Outlook while masquerading as an executable electronic Christmas card. Infected computers can be identified by blue eye icons which appear in the Windows system tray.
Brontok is a computer worm running on Microsoft Windows. It is able to disperse by e-mail. Variants include:
Stration is a family of computer worms that can affect computers running Microsoft Windows, disabling security features and propagating itself to other computers via e-mail attachments. This family of worms is unusual in that new variants are being produced at an unprecedented rate, estimated to be up to one every 30 minutes at its peak, and downloaded from remote servers by infected machines to speed propagation. This makes detection and removal a particular challenge for anti-virus software vendors, because new signature files for each variant need to be issued to allow their software to detect them.

The Storm Worm is a phishing backdoor Trojan horse that affects computers using Microsoft operating systems, discovered on January 17, 2007. The worm is also known as:

MyLife, discovered by MessageLabs in 2002, is a computer worm that spreads itself by sending email to the addresses found in Microsoft Outlook's contacts list. Written in Visual Basic, it displays an image of a girl holding a flower while it attempts to delete files with certain filename extensions. It is named for a phrase appearing in the subject lines of the emails it sends. A variant, MyLife.B, also called the Bill Clinton worm, instead uses a subject line "bill caricature" and displays a cartoon image of Bill Clinton playing a saxophone. Many additional variants have been reported. When the infected file is run, and the picture is closed, the worm runs its payload. MyLife checks the current date. If the minute value is higher or at 45, the worm searches the C:\ directory and deletes .SYS files, .COM files and the same in D:\ Drives.
Koobface is a network worm that attacks Microsoft Windows, Mac OS X, and Linux platforms. This worm originally targeted users of networking websites like Facebook, Skype, Yahoo Messenger, and email websites such as GMail, Yahoo Mail, and AOL Mail. It also targets other networking websites, such as MySpace, Twitter, and it can infect other devices on the same local network. Technical support scammers also fraudulently claim to their intended victims that they have a Koobface infection on their computer by using fake popups and using built-in Windows programs.

Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows OS software and dictionary attacks on administrator passwords to propagate while forming a botnet, and has been unusually difficult to counter because of its combined use of many advanced malware techniques. The Conficker worm infected millions of computers including government, business and home computers in over 190 countries, making it the largest known computer worm infection since the 2003 SQL Slammer worm.
The Pikachu virus, also referred to as Pokey or the Pokémon virus, was a computer worm believed to be the first malware geared at children, due to its incorporation of Pikachu, a creature from the Pokémon media franchise. It was considered similar to the Love Bug, albeit slower in its spread and less dangerous.
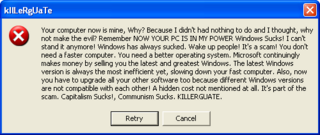
Gruel, also referred to by F-Secure as Fakerr, was a worm first surfacing in 2003 targeting Microsoft Windows platforms such as Windows 9x, Windows ME, Windows 2000 and Windows XP. It spread via email and file sharing networks.






