Related Research Articles

Electronic mail is a method of transmitting and receiving messages using electronic devices. It was conceived in the late–20th century as the digital version of, or counterpart to, mail. Email is a ubiquitous and very widely used communication medium; in current use, an email address is often treated as a basic and necessary part of many processes in business, commerce, government, education, entertainment, and other spheres of daily life in most countries.

An open mail relay is a Simple Mail Transfer Protocol (SMTP) server configured in such a way that it allows anyone on the Internet to send e-mail through it, not just mail destined to or originating from known users. This used to be the default configuration in many mail servers; indeed, it was the way the Internet was initially set up, but open mail relays have become unpopular because of their exploitation by spammers and worms. Many relays were closed, or were placed on blacklists by other servers.

An email client, email reader or, more formally, message user agent (MUA) or mail user agent is a computer program used to access and manage a user's email.
An email address identifies an email box to which messages are delivered. While early messaging systems used a variety of formats for addressing, today, email addresses follow a set of specific rules originally standardized by the Internet Engineering Task Force (IETF) in the 1980s, and updated by RFC 5322 and 6854. The term email address in this article refers to just the addr-spec in Section 3.4 of RFC 5322. The RFC defines address more broadly as either a mailbox or group. A mailbox value can be either a name-addr, which contains a display-name and addr-spec, or the more common addr-spec alone.
Sender Policy Framework (SPF) is an email authentication method designed to detect forging sender addresses during the delivery of the email. SPF alone, though, is limited to detecting a forged sender claim in the envelope of the email, which is used when the mail gets bounced. Only in combination with DMARC can it be used to detect the forging of the visible sender in emails, a technique often used in phishing and email spam.
Greylisting is a method of defending e-mail users against spam. A mail transfer agent (MTA) using greylisting will "temporarily reject" any email from a sender it does not recognize. If the mail is legitimate, the originating server will try again after a delay, and if sufficient time has elapsed, the email will be accepted.
Sender ID is an historic anti-spoofing proposal from the former MARID IETF working group that tried to join Sender Policy Framework (SPF) and Caller ID. Sender ID is defined primarily in Experimental RFC 4406, but there are additional parts in RFC 4405, RFC 4407 and RFC 4408.
Email authentication, or validation, is a collection of techniques aimed at providing verifiable information about the origin of email messages by validating the domain ownership of any message transfer agents (MTA) who participated in transferring and possibly modifying a message.
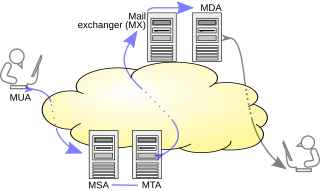
A message submission agent (MSA), or mail submission agent, is a computer program or software agent that receives electronic mail messages from a mail user agent (MUA) and cooperates with a mail transfer agent (MTA) for delivery of the mail. It uses ESMTP, a variant of the Simple Mail Transfer Protocol (SMTP), as specified in RFC 6409.
The Sender Rewriting Scheme (SRS) is a scheme for bypassing the Sender Policy Framework's (SPF) methods of preventing forged sender addresses. Forging a sender address is also known as email spoofing.
Sieve is a programming language that can be used for email filtering. It owes its creation to the CMU Cyrus Project, creators of Cyrus IMAP server.
WHOIS is a query and response protocol that is widely used for querying databases that store the registered users or assignees of an Internet resource, such as a domain name, an IP address block or an autonomous system, but is also used for a wider range of other information. The protocol stores and delivers database content in a human-readable format. The current iteration of the WHOIS protocol was drafted by the Internet Society, and is documented in RFC 3912.
DomainKeys Identified Mail (DKIM) is an email authentication method designed to detect forged sender addresses in email, a technique often used in phishing and email spam.
Domain-based Message Authentication, Reporting and Conformance (DMARC) is an email authentication protocol. It is designed to give email domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. The purpose and primary outcome of implementing DMARC is to protect a domain from being used in business email compromise attacks, phishing email, email scams and other cyber threat activities.
Email forwarding generically refers to the operation of re-sending an email message delivered to one email address to one or more different email addresses.

A feedback loop (FBL), sometimes called a complaint feedback loop, is an inter-organizational form of feedback by which a mailbox provider (MP) forwards the complaints originating from their users to the sender's organizations. MPs can receive users' complaints by placing report spam buttons on their webmail pages, or in their email client, or via help desks. The message sender's organization, often an email service provider, has to come to an agreement with each MP from which they want to collect users' complaints.
The Abuse Reporting Format (ARF) also known as the Messaging Abuse Reporting Format (MARF) is a standard format for reporting spam via email.
People tend to be much less bothered by spam slipping through filters into their mail box, than having desired e-mail ("ham") blocked. Trying to balance false negatives vs false positives is critical for a successful anti-spam system. As servers are not able to block all spam there are some tools for individual users to help control over this balance.
A mailbox provider, mail service provider or, somewhat improperly, email service provider is a provider of email hosting. It implements email servers to send, receive, accept, and store email for other organizations or end users, on their behalf.
Murray S. Kucherawy is a computer scientist, mostly known for his work on email standardization and open source software.
References
- ↑ Felix Schwagereit; Ansgar Scherp; Steffen Staab (June 14–17, 2011). Survey on Governance of User-generated Content in Web Communities (PDF). WebSci'11. ACM . Retrieved 2012-01-04.
- ↑ "Hash-Sharing Systems". wiki. Apache Foundation . Retrieved 15 August 2012.
- ↑ Jason Livingood; Nirmal Mody; Mike O'Reirdan (March 2012). Recommendations for the Remediation of Bots in ISP Networks. IETF. doi: 10.17487/RFC6561 . RFC 6561 . Retrieved 15 August 2012.
- ↑ "Email Feedback Loop: What It Is and Why It Matters [2023]". mailtrap.io. 2023-03-01. Retrieved 2023-04-18.
- ↑ Murray Kucherawy, ed. (June 2012). Creation and Use of Email Feedback Reports: An Applicability Statement for the Abuse Reporting Format (ARF). IETF. doi: 10.17487/RFC6650 . RFC 6650 . Retrieved 28 June 2012.
Rather than generating feedback reports themselves, MUAs SHOULD create abuse reports and send these reports back to their Mailbox Providers so that they can generate and send ARF messages on behalf of end users (see Section 3.2 of [RFC6449]). This allows centralized processing and tracking of reports, and provides training input to filtering systems.
- ↑ Theo Clarke (10 October 2005). "Finding network abuse contacts". Wikimedia Foundation . Retrieved 22 April 2011.
- ↑ John R. Levine (9 December 2009). "Adding a spam button to MUAs". ASRG mailing list (Mailing list). Retrieved 22 April 2011. See also the wiki summary of that mail thread.
- ↑ J.D. Falk, ed. (November 2011). Complaint Feedback Loop Operational Recommendations. IETF. doi: 10.17487/RFC6449 . RFC 6449 . Retrieved 18 November 2011.
Appendix B. Using DKIM to Route Feedback
- ↑ "Community Consultation Underway - Removal of WHOIS Query Result Limit". ARIN. 2007-03-12. Retrieved 2009-09-28.
[T]he ARIN WHOIS query limit of 256 results [...] has been in place since ARIN's inception as a means of curtailing data mining.
- ↑ Leslie Nobile (18 July 2011). "Abuse Contact To Be Mandatory per Policy 2010-14". announcements. American Registry for Internet Numbers . Retrieved 24 August 2011.
- ↑ Tobias Knecht (8 November 2010). "Abuse contact information". Asia-Pacific Network Information Centre . Retrieved 22 April 2011.
- ↑ One is Abusehelper